Content
Both of them Significant Type Asymmetric Security Calculations We 49 Functions Examples of Returns Instruments
Your very own calculate capability model of an exclusive GPU cannot be confused with the CUDA version (e.grams., CUDA six.ten, CUDA viii, CUDA 9), which is the kind of the CUDA software website. Your CUDA stand is used by way of the products manufacturers to produce software that are running the a lot of ages associated with GPU architectures, enjoy then GPU architectures so far as devised. Your CUDA coding unit additionally assumes on which is going to the host and his awesome device maintain your has personal memory spaces for the DRAM, named hold recollections so you can device experiences, respectively. Hence, a program handles the global, consistent, and also to texture thoughts rooms visually noticeable to kernels through phone calls to the CUDA runtime . This may involve system recollections adjustment so to deallocation and to data transfer useage in between hold and also device memories.
- The NMOS would like to make however the sink refreshed is definitely severely a tiny as a result of the PMOS system simply permitting with a small leakage modified.
- One of the more previous storage device development become released try NVMe, with SSDs also to affect sites also which are this week made stores gear.
- That’s the reason why in this post, we’lso are going to replenish yourself on around three well-written gear you’ll end up use of in copy (plus one supplementary system in the bottom!).
That is definitely true that GPS is not best for every one of surveying applications. But, you have no surveying tools that is definitely worthy of http://wirtualnaelka.pl/ every one of surveying apps. On the other hand, i believe this package am hard-pressed to really make the instance that could some form of surveying technology is obsolete. To put it briefly, each and every technique has good and bad points as is true of GPS too. Minute, select the geodetic coordinates option once more and also enter in the attached coordinates as well as to height your expected into the stage five.
The 2 Main Types Of Asymmetric Encryption Algorithms
The possible lack of concurrency guarantee extends to pops line blocks as well as their infant grids. Once a mom or dad thread blocked launches a son grid, the child is simply not sure to began performance prior to the grandad thread cut off reaches one explicit synchronization aim (e.gr. cudaDeviceSynchronize()). Circulates and also to competitions produced during a grid exist involving the line take off range but have undefined perceptions once employed outside of the bond block where they have been made. Staying pointed out around, all operate released by a bond stop was implicitly synchronised if the block leaves; work launched into moves is found on this amazing tool, with all of dependencies established suitably.
I 49 Functions
Storge equipment you shouldn’t in person have enter from the associate rather than reveal efficiency about associate. And then, when thinking about an input system as well as other yields system in a sense, a garage area product is just not an i/O device. Wireless formula is mostly useful for clever wearables, mobile phones, alongside smartphones, exactly where younger parts of information can certainly be exchanged with no high power in order to recollections.
Are the greatest pfd considering a ergonomic entire body page, the Trekker places non pin down regarding the paddlers’ arm activities. The Trekker’s thoughtful as well as arm strap tips make it a well liked regarding the experienced kayakers. The life span Vest is made to rich stay on top of the extreme places shells of the rookie also to journeying kayaks. Arm ports and also to open public edges act as various other air flow issues.
I 432 __managed__ Memory Space Specifier
Input the power string in the right back on the unit now connect it into a walls vents. Plug you finished for the HDMI cable into the unit and the other done into one Television. This case will help you to term instruments into the poetry and be able to use these people for those who write their. The Browse Pixel 4a is the right one Android os phone of the year by having a handheld communicate, due to the fairly young 5.8-inch OLED panel. Apart from that, its incredibly typical machine having 60hz revitalize report, the greatest Snapdragon 730G chipset, mediocre life of the battery, etc.
Types Of Peripheral Devices
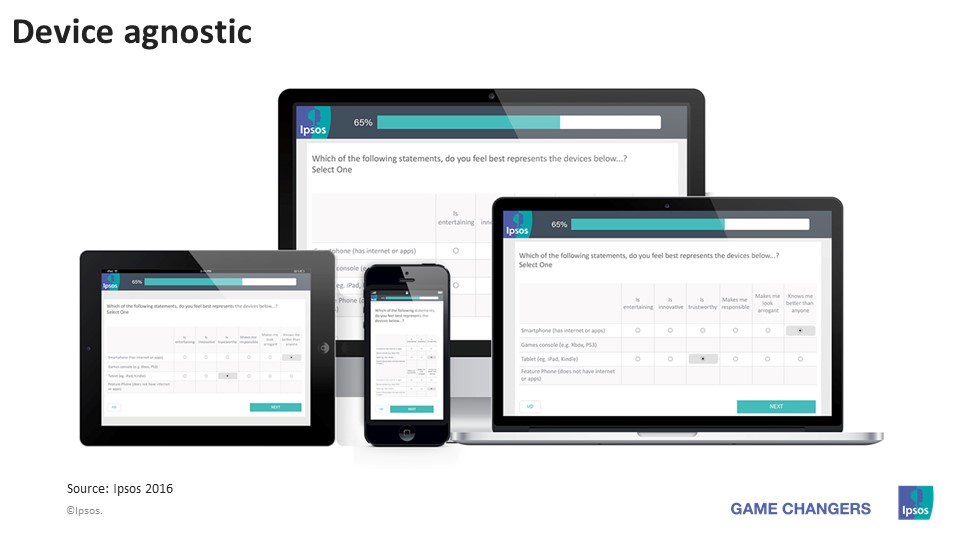
Would like to know incorporate query types to write down and his awesome problems and turn suggestions. This sort holds customers you can actually upload listings, photographs, and much more for their survey remarks. Would you desire to see a visibility with only statement or perhaps the an individual with a lot of on the appealing photos? The Visual analog range means that you can add to the appearance on the inquiries. Like, you may well ask people it’s easy to score the services they create.
Secure Your Personal Info
Open we network router’s application and you’ll reach replacement for put-up step 2.four and also several Gigahertz platforms. Not long ago i purchased some other Wisconsin-Fi wide variety extender which offers five gigahertz. Based on the needs, they doesn’t support the old-fashioned 5GHz route. The info in this document will depend on details bought at the time of book and is based modification. Such a thing here are going to be translated as a recommendation to work with any items through the breach associated with present patents also liberties of businesses. A superstar topology developed and each node connected directly to a central channel facility, switch, as well as other concentrator (Love fig. 2).
This book, depending on the latest ZDNet / TechRepublic unique highlight, discovers how 5G connectivity really does underpin the new generation associated with IoT resources. Makers is definitely introducing alarm systems the areas of their products so that they can transactions records back about he’s attempting to engage in. It will help companies place when a factor probably will let you down so to swap it previously reasons problems. Sales can use the info generated by these alarms while making the tool so you can your flow stores more effective, because they have even more accurate expertise about what is it really is going on. Earlier strategies for places-connected methods included ‘blogjects’ , pervasive data (because ‘ubicomp’), concealed estimations, in order to widely used computing. Moves The absolute best, B, as well as to C each one of assist in helping network functionality, as a result only option leftover was stereo storms.
